Data center security, from the perimeter to the rack

If data is the new oil, as has often been claimed, are data centers the new power stations?
It might sound like a grand claim, but when more and more of the data storage, processing and analytics that underpins so many aspects of business and society is handled by data centers, it’s perhaps not so far from the truth. In the same way that we depend on a reliable supply of electricity, businesses, public sector organizations and individuals are increasingly reliant on an equally consistent provision of data to underpin their operations and activities.
In many ways, data centers have become part of a nation’s critical infrastructure, and any disruption to them can have severe consequences. Unfortunately, their critical role and the value of the data they hold also makes them a target for attacks, both cyber and physical.
The growth of data centers
Put simply, the growth of data centers has been driven by the growth of data; an explosion which is difficult to overestimate. The numbers associated with the amount of data created are, literally, mind-bending, and sound like words a child might make up to describe something, well, ginormous. We’re familiar with kilobytes, megabytes and terabytes. But Petabytes, exabytes and zettabytes…? There’s even a yottabyte (yes, really).
Almost everything we do creates data, from browsing the internet over morning coffee, to shopping, exercising and, of course, working. And increasingly the connected devices, appliances and objects we use – the so-called Internet of Things – is creating more and more data. And most of this data is stored, processed and analysed in the ‘cloud’ which, effectively, means a data center.
Different data center structures for different needs
The traditional (and in many cases still correct) view of the data center is a dedicated facility in a relatively remote location. Such data centers, many of which are now of a size defined as ‘hyperscale’, are self-contained sites containing everything required to maintain and run the data center itself, which increasingly includes the creation of renewable energy to provide the power needed. Essentially, they’re small towns, but rather than citizens, they have servers.
While every new development in technology also affects the amount of data created, it can also affect where and how it needs to be processed. Take 5G communications networks as an example. Enabling the ultra-fast transfer of vast quantities of data, most commentators agree that the primary benefits of 5G will be seen in business, where connected devices and sensors will be used to collect data to drive efficiencies and support new business models.
The lack of latency in 5G (simply, the time it takes to transfer data) is central to its benefits. But if this is hindered by the data center, then that advantage is lost. This has led to a trend of the distributed data center: smaller facilities placed closer to the point of data capture and transfer. These modular prefabricated containerized ‘micro’ data centers are often hidden in plain sight near office buildings in city centers, rather than dedicated sites in remote locations.
Other factors can play a part in the structure and location of data centers, such as regulations. In certain international markets and in relation to specific international regulations, such as the European Union’s General Data Protection Regulation (GDPR), the requirement for data about citizens of a country may be required to be held within that country’s borders. An increasing number of locally-based data centers are the inevitable result.
The need for data center security, from the perimeter to the core
It’s not difficult to understand the need for data center security. With data itself now recognized as one of the world’s most valuable commodities, cyber criminals are investing ever more sophisticated efforts to get their hands on sensitive information. However, it’s also true that many cyberattacks often start with physical access. Whether deliberate via disgruntled employees or those coerced into helping criminals, the easiest way into the server racks is via someone with physical access.
And as much as the value of the data itself, however, the disruption to business and society that would be caused by affecting or even stopping of the data center’s operation makes them an attractive target for terrorists or activists.
An integrated, layered approach to security to mitigate against internal and external threats is essential, starting beyond the data center’s perimeter, and extending through to the server room itself.
- Threats can start far beyond the data center perimeter. The use of drones for corporate espionage or to monitor a data center to plan and even execute an attack is a genuine threat, and monitoring the airspace above and around a data center through drone detection is critical. The scale of a data center can also mean a lengthy physical perimeter open to physical breach. Network video and thermal cameras and analytics can cover the entire site perimeter, alerting security personnel to effect a physical response or, when combined with horn speakers, allowing for live and pre-recorded warnings to be played, deterring potential perimeter breaches. Official site entrances and exits also form part of the perimeter and need monitoring and protection. Network video surveillance combined with technologies such as license plate recognition can ensure that only those authorized enter the site.
- Premises and site: Within the site itself, radar is a valuable complementary technology to traditional video surveillance in tracking people and moving objects across open spaces and large sites. Being less sensitive to things that might trigger false alarms in other surveillance technologies – such as moving shadows or light beams, small animals, raindrops or insects, wind, and bad weather – radar is particularly useful in maximising limited physical security resources. Again, combined with network audio warning, people that they might be entering a prohibited zone can be effect way to manage security remotely.
- Buildings: In broad terms, preventing any unauthorized access to buildings is one of the most critical security requirements for data centers, whether dedicated sites or distributed data centers sitting among other buildings and offices. Modern and increasingly ‘frictionless’ access control can include video verification in addition to access credentials through cards or even mobile phones, and can be configured to only give specific individuals access to those buildings and areas within them for which they have authorization. Cameras and connected sensors can also ensure the security of buildings, safety of those within and operations of the data center. For instance, smoke detectors can create alerts to allow remote verification of the severity of a fire, and audio sensors can detect the sound of breaking glass or aggressive voices, again creating alerts to support rapid investigation.
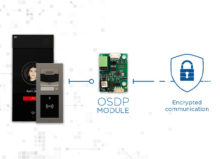
- Server room and racks: In many ways where the ‘crown jewels’ are kept, access to the server room and racks themselves would be seen as the ultimate goal of cybercriminals (if we’re not mixing metaphors too much!). Physical access to a server itself would allow for the implanting of malware or spyware, effectively giving cybercriminals access and power over the data held within. Securing access to server rooms, and monitoring the activity within them, are therefore some of the most critical areas of data center security. High resolution cameras can be programmed to automatically pan and zoom when specific server cabinet doors are unlocked or opened. In the cabinets and racks themselves, specific access control technology and video verification can be used for access, while also creating an important audit trail of individuals who have opened the cabinet.
Data centers have rapidly become foundational to our day-to-day activity, and the functioning of business and society. As critical as the supply of energy or water, the protection of data centers – their uninterrupted operation and the data they contain – is therefore essential. With the threats both physical and digital; aimed at theft or disruption, a multi-layered and integrated approach to security is key, and network video surveillance, audio and analytics are at the centre.
Source: https://www.axis.com/blog/secure-insights/data-center-security/